Border Gateway Protocol Hijacking
What is BGP?
BGP stands for Border Gateway Protocol, and it is the routing protocol of the Internet. In other words, it provides directions so that traffic travels from one IP address to another as efficiently as possible. An IP address is the actual web address of a given website. When a user types in a website name and the browser finds and loads it, requests and responses go back and forth between the user's IP address and the IP address of the website. DNS (domain name system) servers provide the IP address, but BGP provides the most efficient way to reach that IP address. Roughly speaking, if DNS is the Internet's address book, then BGP is the Internet's road map.
What Is BGP Hijacking?
BGP hijacking is when attackers maliciously reroute Internet traffic. Attackers accomplish this by falsely announcing ownership of groups of IP addresses, called IP prefixes, that they do not actually own, control, or route to. A BGP hijack is much like if someone were to change out all the signs on a stretch of freeway and reroute automobile traffic onto incorrect exits.
Definition of an autonomous system (AS)
An autonomous system is a large network or group of networks managed by a single organization. An AS may have many subnetworks, but all share the same routing policy. Usually an AS is either an ISP or a very large organization with its own network and multiple upstream connections from that network to ISPs (this is called a 'multihomed network'). Each AS is assigned its own Autonomous System Number, or ASN, to identify them easily.
How can BGP be hijacked?
When an AS announces a route to IP prefixes that it does not actually control, this announcement, if not filtered, can spread and be added to routing tables in BGP routers across the Internet. From then until somebody notices and corrects the routes, traffic to those IPs will be routed to that AS. It would be like claiming territory if there were no local government to verify and enforce property deeds.
BGP always favors the shortest, most specific path to the desired IP address. In order for the BGP hijack to be successful, the route announcement must either:
1) Offer a more specific route by announcing a smaller range of IP addresses than other ASes had previously announced.
2) Offer a shorter route to certain blocks of IP addresses. Additionally, not just anyone can announce BGP routes to the larger Internet. In order for a BGP hijack to occur, the announcement must be made by the operator of an AS, or by a threat actor who has compromised an AS (the second case is more rare).

The Internet Routing Registries (IRR)
The Internet Routing Registries (IRR) are semi-public databases used by network operators to register their assigned Internet resources. Some database maintainers do not check whether the entry was actually made by the owner, nor check if the prefix has been transferred to somebody else. This makes them prone to error and not completely reliable.
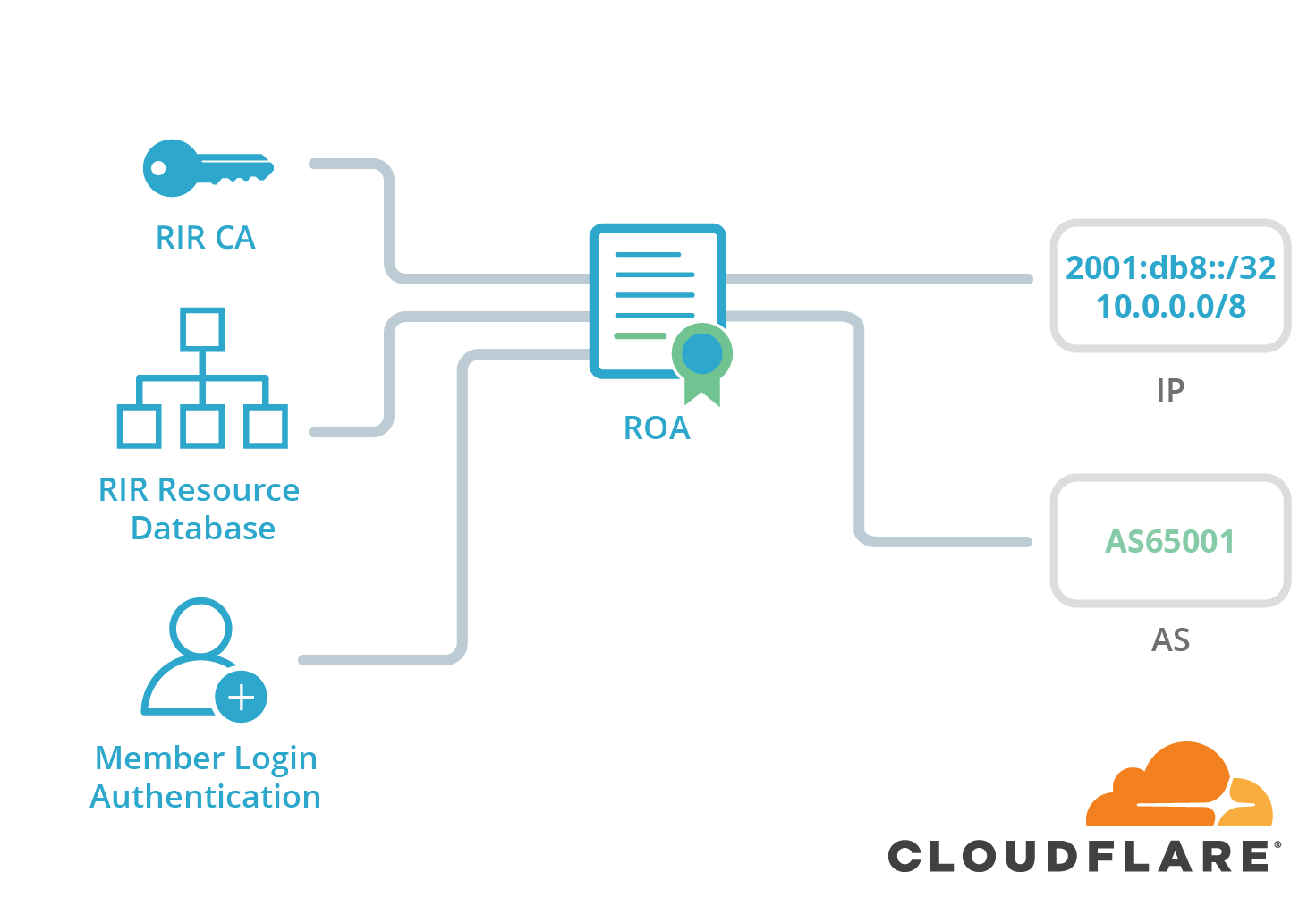
Resource Public Key Infrastructure (RPKI)
Resource Public Key Infrastructure (RPKI) is similar to the IRR “route” objects, but adding the authentication with cryptography.
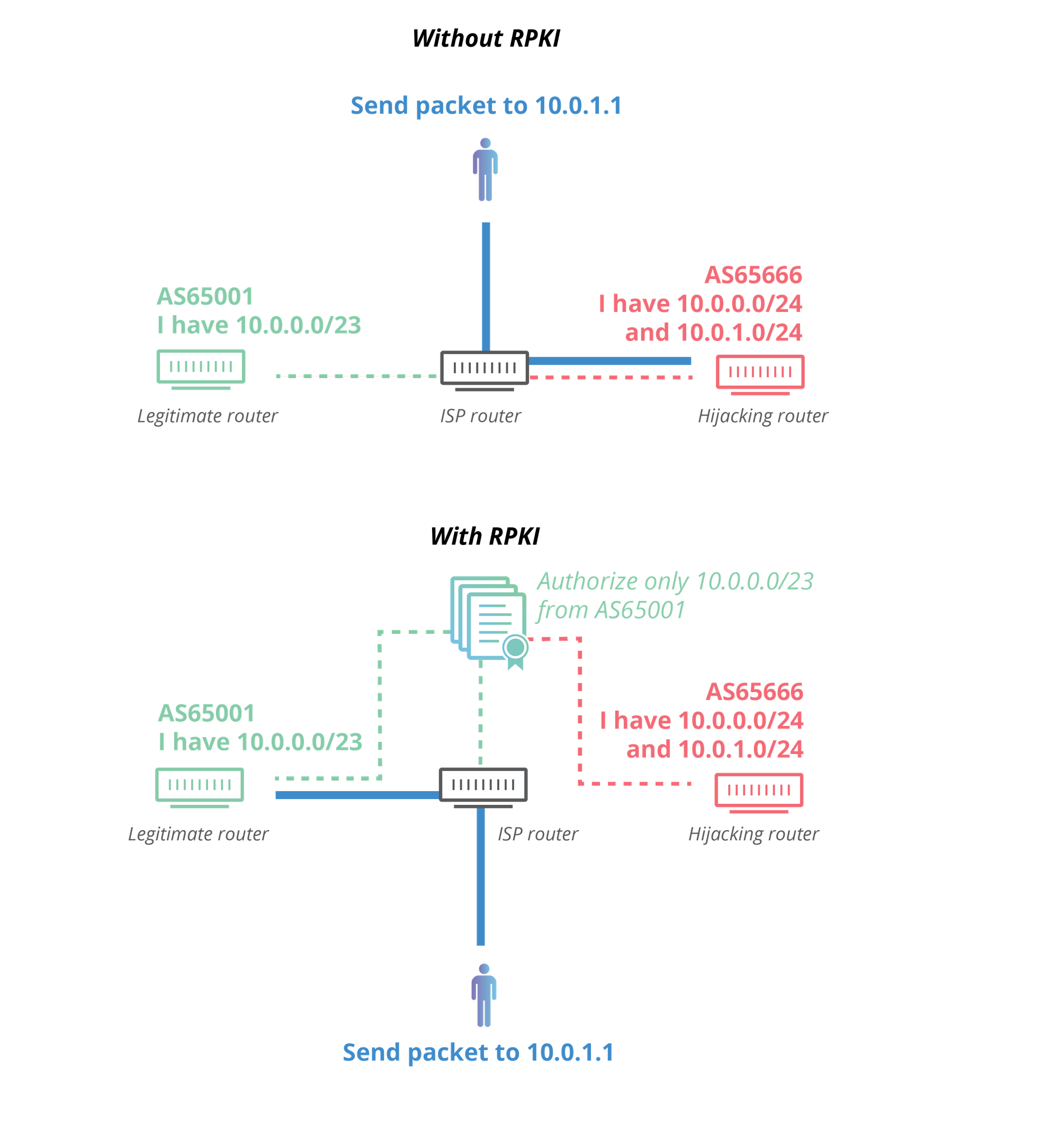
Enforcing validated prefixes
Signing the prefixes is one thing. But ensuring that the prefixes we receive from our peers match their certificates is another.
The first part is validating the certificate chain. It is done by synchronizing the RIR databases of ROAs through rsync (although there are some new proposals regarding distribution over HTTPS), then check the signature of every ROA against the RIR’s certificate public key. Once the valid records are known, this information is sent to the routers.
Major vendors support a protocol called RPKI to Router Protocol (abbreviated as RTR). This is a simple protocol for passing a list of valid prefixes with their origin ASN and expected mask length. However, while the RFC defines 4 different secure transport methods, vendors have only implemented the insecure one. Routes sent in clear text over TCP can be tampered with.

Signing prefixes
Each network operator owning and managing Internet resources (IP addresses, Autonomous System Numbers) has access to their Regional Internet Registry portal. Signing their prefixes through the portal or the API of their RIR is the easiest way to start with RPKI.
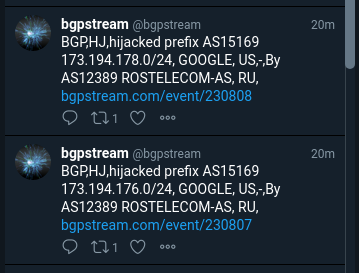
Russian telco hijacks internet traffic for Google, AWS, Cloudflare, and others
Earlier this week, traffic meant for more than 200 of the world's largest content delivery networks (CDNs) and cloud hosting providers was suspiciously redirected through Rostelecom, Russia's state-owned telecommunications provider.
The incident affected more than 8,800 internet traffic routes from 200+ networks, and lasted for about an hour.
Impacted companies are a who's who in the cloud and CDN market, including big names such as Google, Amazon, Facebook, Akamai, Cloudflare, GoDaddy, Digital Ocean, Joyent, LeaseWeb, Hetzner, and Linode.
Sources:
What is BGP hijacking? | Cloudflare
RPKI and BGP: our path to securing Internet Routing
Is BGP Safe Yet? No. But we are tracking it carefully
Russian telco hijacks internet traffic for Google, AWS, Cloudflare, and others