Mitgating a DDoS/DoS attack
A denial-of-service (DoS) attack floods a server with traffic, making a website or resource unavailable. A distributed denial-of-service (DDoS) attack is a DoS attack that uses multiple computers or machines to flood a targeted resource. Both types of attacks overload a server or web application with the goal of interrupting services.
As the server is flooded with more Transmission Control Protocol/User Datagram Protocol (TCP/UDP) or other protocols packets than it can process, it may crash, the data may become corrupted, and resources may be misdirected or even exhausted to the point of paralyzing the system.
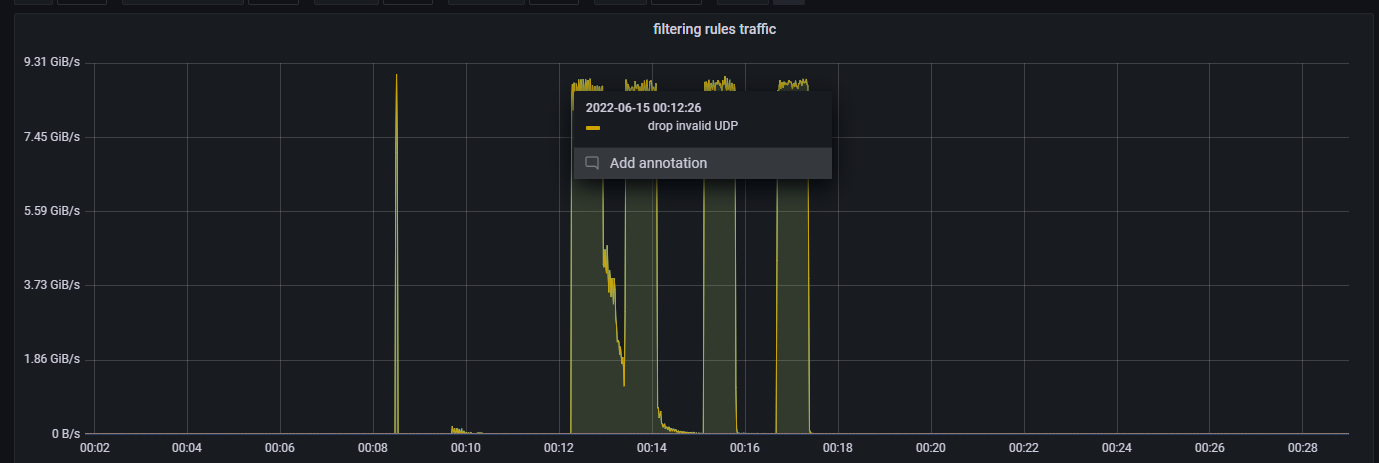
I've developped a multi sequence filtering rule based on the "zero trust" concept to filter up to 99,9% of malicious traffic on the specified port ranges, those filtering rules were developped using the BPF library and the malicious traffic was dropped using the XDP technology which in a few words, loaded in "skb" mode, loads the code before the linux kernel in order to drop packets before processing them, by doing that I can drop up to 10 millions packets per second per core.
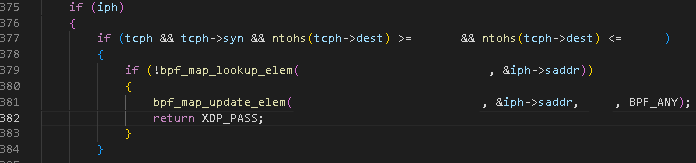
The filter's code is confindential, but I will leave a sneak peek with the beginning code from one of my filters that I've programmed.
The filtering rule in action (visualization made using Grafana):